Burp Suite: a helpful tool for testing of client-server software
As a test engineer, I often need to see what requests applications are making and what responses they are receiving. While browsers offer developer tools that include network monitoring, I find them inconvenient. Additionally, you can't use them with mobile and desktop software.
Recently, I discovered Burp Suite, a tool for security assessment and penetration testing that comes with many useful features. Although the professional edition is quite expensive, the free community edition is sufficient for regular testing activities.
Key functionality
- A proxy server to intercept traffic.
- A convenient user interface to analyze network activity.
- The ability to modify and repeat requests.
- The option to store individual requests for future use; however, the history is erased in the community edition when you close the program.
- A text decoder that automatically translates strings like
"%7B%22key%22:%22value%22%7D"to{"key":"value"}.
Configuration
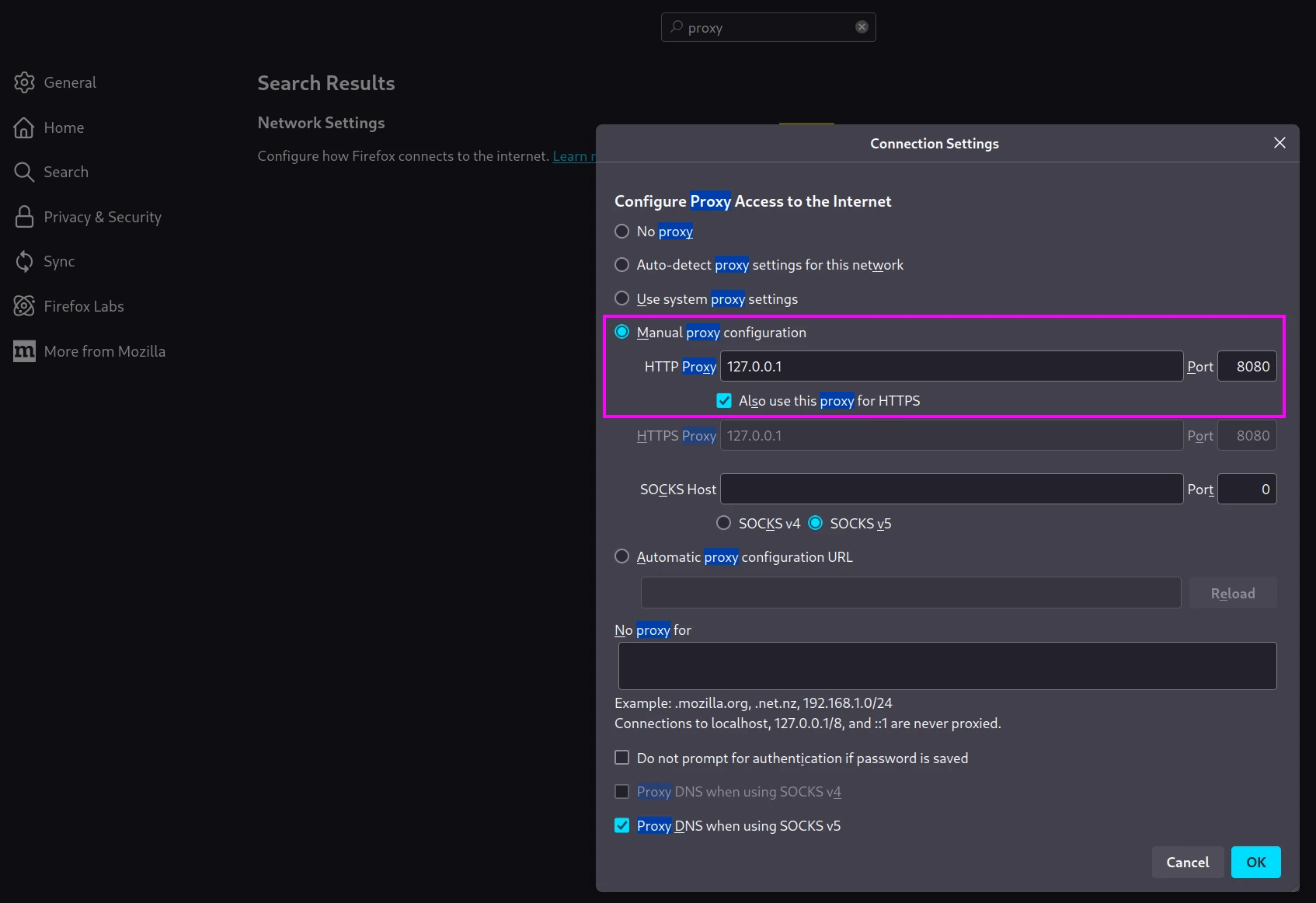
If you're testing a web application, you'll need to configure your browser to use Burp Suite as a proxy. By default, it listens at 127.0.0.1:8080.
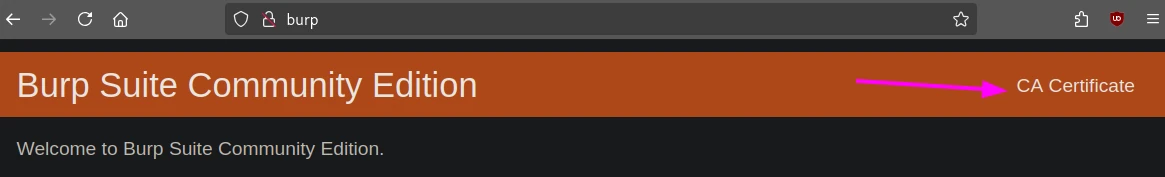
Next, navigate to http://burp and download a certificate.
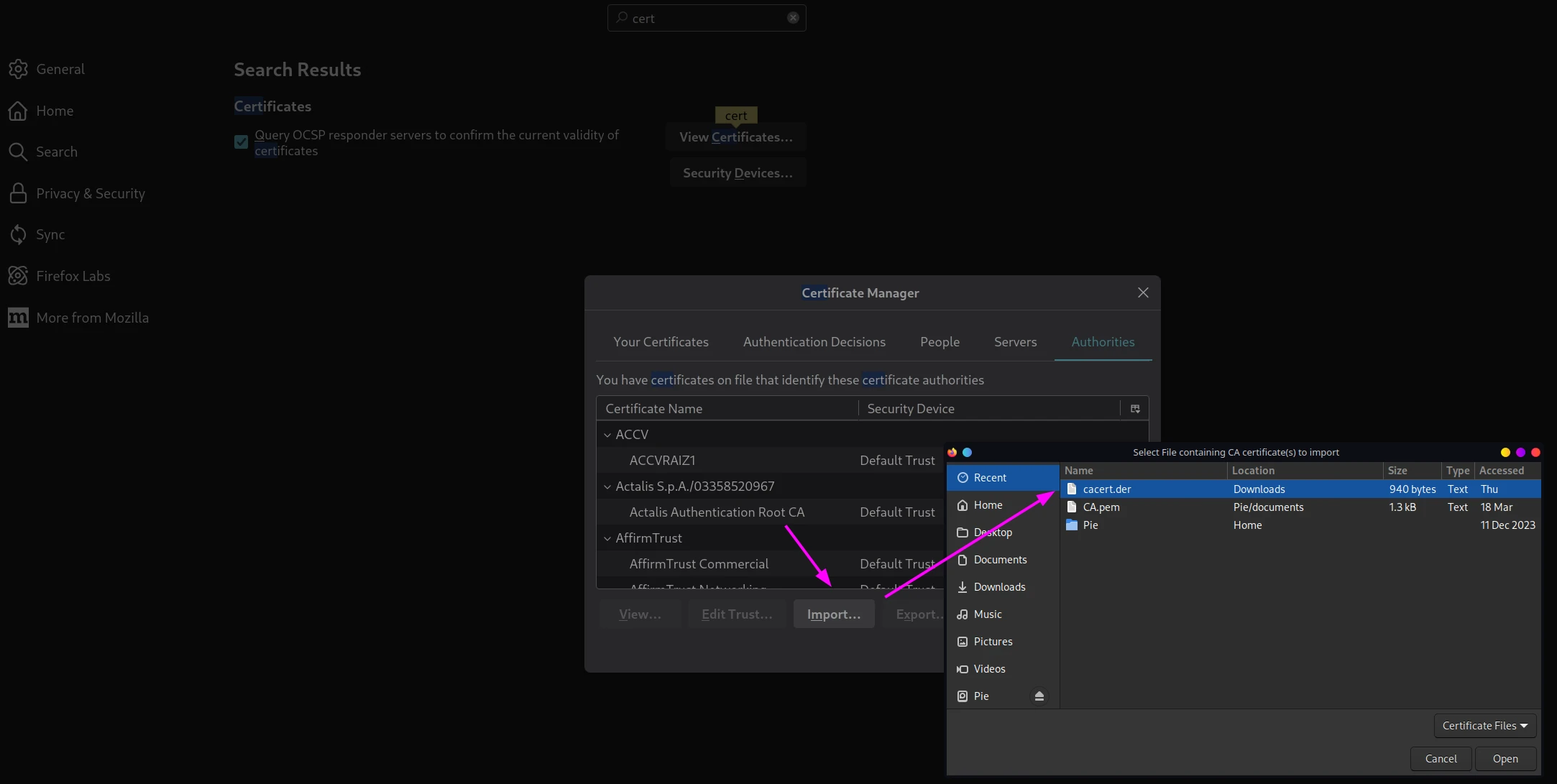
Finally, import the certificate into Firefox. This will make it possible to intercept HTTPS traffic.
Here are the official instructions for setting up Burp Suite on mobile devices:
Unfortunately, there is a caveat with Android. Google services will not accept this certificate unless you have a rooted device and install it as a root, which can be complicated or even impossible. However, for user-level software, this isn't a problem. As for iOS, I don't have much experience with it, but similar to Android, there are no issues with non-system programs.
Usage
Once Burp Suite is running and the proxy is configured, try navigating to a website. I'll use thinking-tester-contact-list.herokuapp.com, I mentioned it in my post How to mock server responses while testing web apps with Playwright? To use it, you'll need to register first.
Let's fill the login form and click submit.
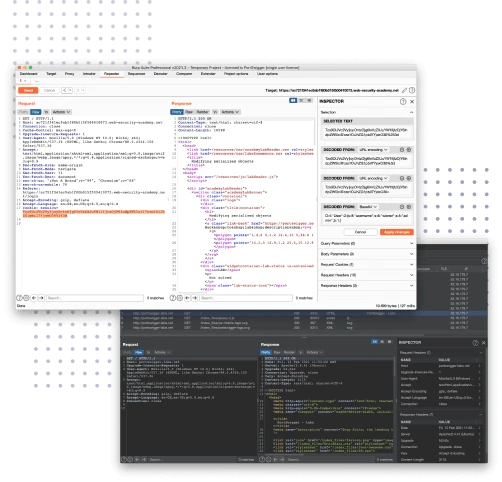
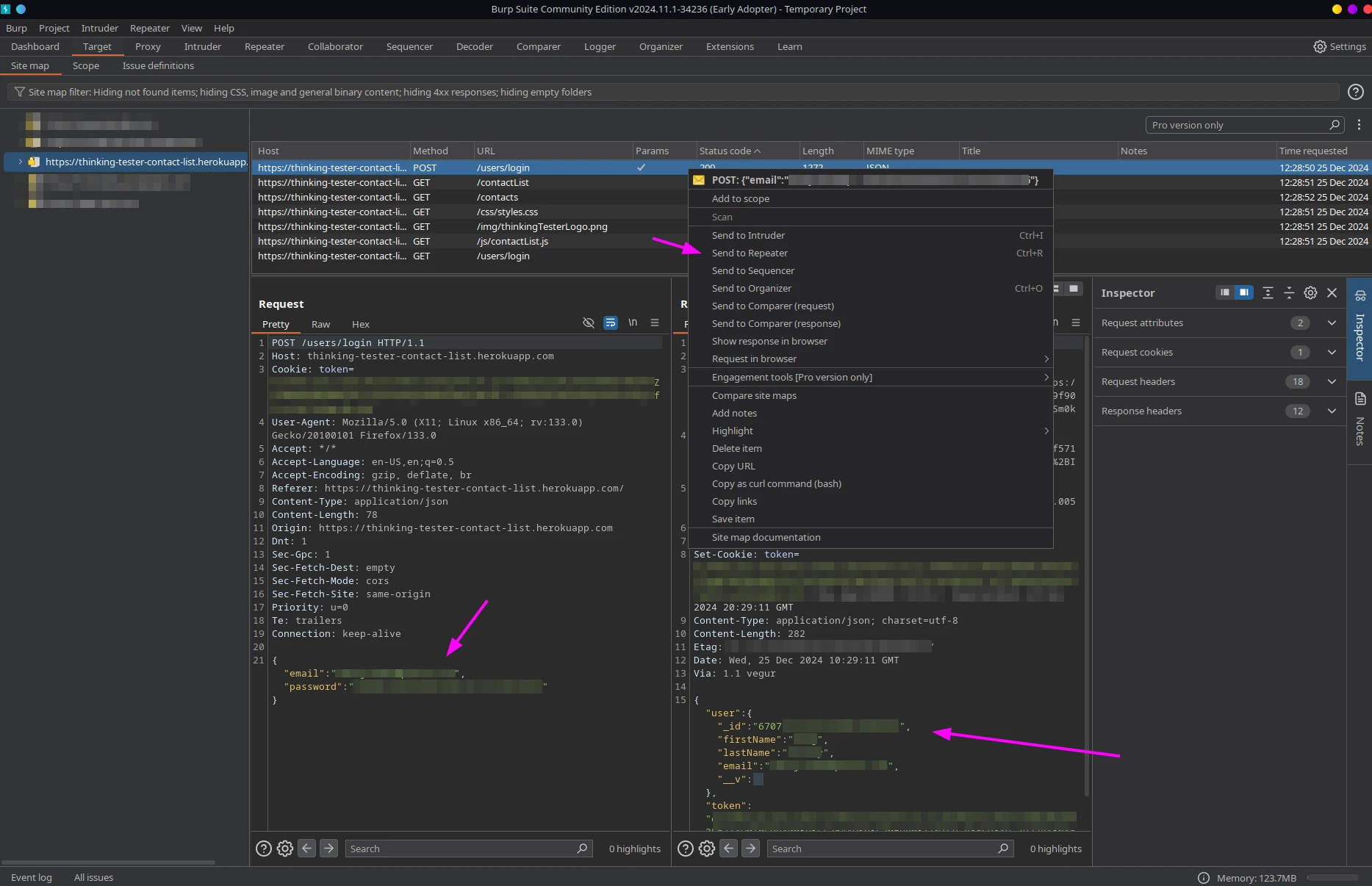
Now, navigate to Burp Suite -> Target -> Site map. On the left, you'll see a list of hosts that the browser has called. This application's https://thinking-tester-contact-list.herokuapp.com/ will be among them.
The layout is similar to what you see in a browser or in API testing tools like Insomnia, with queries at the top and request and response bodies at the bottom. Here, we can see that the email/password combination was posted to /users/login as json. Since my credentials were valid, the server returned me some user data and a token that can be used for subsequent API calls.
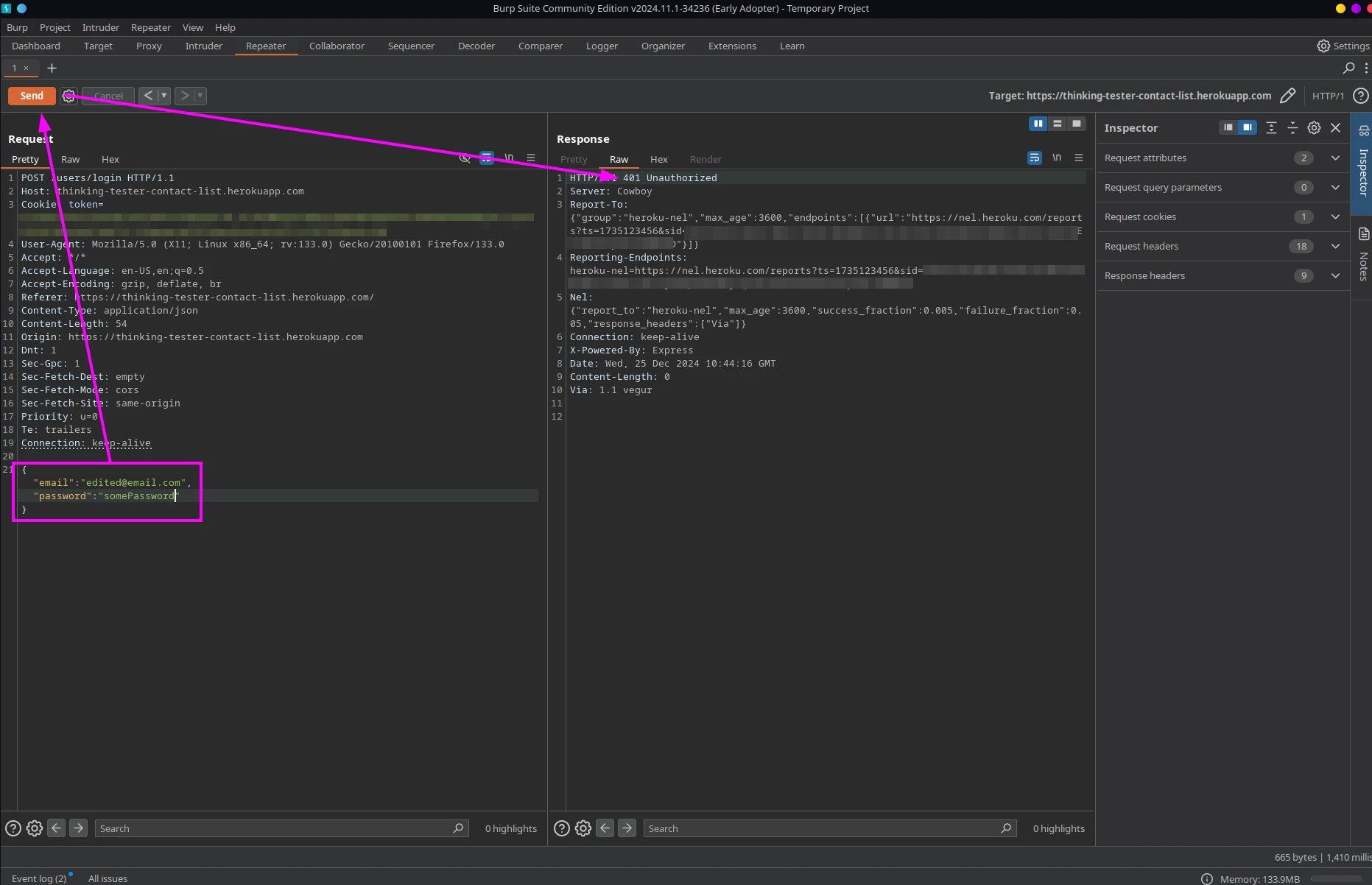
We can also send this request to the Repeater to manipulate and resend it. For instance, we can modify the credentials, send the request, and see what happens. In this case, the server returned a 401 status code - the login attempt wasn't successful.
To validate this case, we could easily use the web form. However, for more sophisticated testing this isn't always possible. We might need to send prohibited symbols, but the frontend wouldn't even allow us to type them. Other test scenarios might require us to execute a long list of pre-steps first, after which the browser would redirect us elsewhere upon form submission with no option to return to the previous state.
In these situations, having an interceptor that can capture all requests and allows us to edit them is extremely helpful. This is especially true for desktop and mobile applications. If you keep the proxy on, you can always come back to queries made hours or days ago. That's why I find Burp Suite so handy! I recommend giving it a try if you work with client-server architecture.